Last Updated on May 3, 2018 by Admin
8.3.1.2 Packet Tracer – CCNA Skills Integration Challenge
From year to year, Cisco has updated many versions with difference questions. The latest version is version 6.0 in 2018. What is your version? It depends on your instructor creating your class. We recommend you to go thought all version if you are not clear. While you take online test with netacad.com, You may get random questions from all version. Each version have 1 to 10 different questions or more. After you review all questions, You should practice with our online test system by go to "Online Test" link below.
Packet Tracer – CCNA Skills Integration Challenge
Answer Note: Red font color or gray highlights indicate text that appears in the Answer copy only.
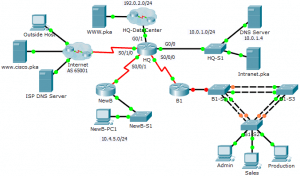
Topology
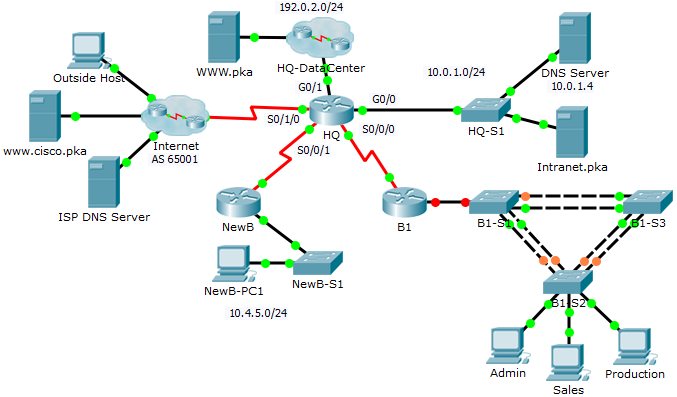
8.3.1.2 Packet Tracer – CCNA Skills Integration Challenge
Addressing Table
| Device | Interface | IP Address | Subnet Mask |
| HQ | G0/0 | 10.0.1.1 | 255.255.255.0 |
| G0/1 | 192.0.2.1 | 255.255.255.0 | |
| S0/0/0 | 10.255.255.1 | 255.255.255.252 | |
| S0/0/1 | 10.255.255.253 | 255.255.255.252 | |
| S0/1/0 | 209.165.201.1 | 255.255.255.252 | |
| B1 | G0/0.10 | 10.1.10.1 | 255.255.255.0 |
| G0/0.20 | 10.1.20.1 | 255.255.255.0 | |
| G0/0.30 | 10.1.30.1 | 255.255.255.0 | |
| G0/0.99 | 10.1.99.1 | 255.255.255.0 | |
| S0/0/0 | 10.255.255.2 | 255.255.255.252 | |
| B1-S2 | VLAN 99 | 10.1.99.22 | 255.255.255.0 |
VLAN Configurations and Port Mappings
| VLAN Number | Network Address | VLAN Name | Port Mappings |
| 10 | 10.1.10.0/24 | Admin | F0/6 |
| 20 | 10.1.20.0/24 | Sales | F0/11 |
| 30 | 10.1.30.0/24 | Production | F0/16 |
| 99 | 10.1.99.0/24 | Mgmt&Native | F0/1-4 |
| 999 | N/A | BlackHole | Unused Ports |
Scenario
In this comprehensive CCNA skills activity, the XYZ Corporation uses a combination of eBGP and PPP for WAN connections. Other technologies include NAT, DHCP, static and default routing, EIGRP for IPv4, inter-VLAN routing, and VLAN configurations. Security configurations include SSH, port security, switch security, and ACLs.
Note: Only HQ, B1, B1-S2, and the PCs are accessible. The user EXEC password is cisco and the privileged EXEC password is class.
Requirements
PPP
- Configure the WAN link from HQ to the Internet using PPP encapsulation and CHAP authentication.
- Create a user ISP with the password of cisco.
- Configure the WAN link from HQ to NewB using PPP encapsulation and PAP authentication.
- Create a user NewB with the password of cisco.
Note: The ppp pap sent-username is not graded by Packet Tracer. However, it must be configured before the link will come up between HQ and NewB.
HQ(config)# interface s0/1/0 HQ(config-if)# encapsulation ppp HQ(config-if)# ppp authentication chap HQ(config-if)# exit HQ(config)# username ISP password cisco HQ(config)# interface s0/0/1 HQ(config-if)# encapsulation ppp HQ(config-if)# ppp authentication pap HQ(config-if)# ppp pap sent-username HQ password cisco HQ(config-if)# exit HQ(config)# username NewB password cisco
eBGP
- Configure eBGP between HQ and the Internet.
- HQ belongs to AS 65000.
- The IP address for the BGP router in the Internet cloud is 209.165.201.2.
- Advertise the 192.0.2.0/24 network to the Internet.
HQ(config)# router bgp 65000 HQ(config-router)# neighbor 209.165.201.2 remote-as 65001 HQ(config-router)# network 192.0.2.0 mask 255.255.255.0
NAT
- Configure dynamic NAT on HQ
- Allow all addresses for the 10.0.0.0/8 address space to be translated using a standard access list named NAT.
- XYZ Corporation owns the 209.165.200.240/29 address space. The pool, HQ, uses addresses .241 to .245 with a /29 mask. Bind the NAT ACL to the pool HQ. Configure PAT.
- The connections to the Internet and HQ-DataCenter are outside XYZ Corporation.
HQ(config)# ip access-list standard NAT HQ(config-std-nacl)# permit 10.0.0.0 0.255.255.255 HQ(config-std-nacl)# exit HQ(config)# ip nat pool HQ 209.165.200.241 209.165.200.245 netmask 255.255.255.248 HQ(config)# ip nat inside source list NAT pool HQ overload HQ(config)# interface s0/1/0 HQ(config-if)# ip nat outside HQ(config-if)# interface g0/1 HQ(config-if)# ip nat outside HQ(config-if)# interface s0/0/0 HQ(config-if)# ip nat inside HQ(config-if)# interface s0/0/1 HQ(config-if)# ip nat inside HQ(config-if)# interface g0/0 HQ(config-if)# ip nat inside
Inter-VLAN Routing
- Configure B1 for inter-VLAN routing.
- Using the addressing table for branch routers, configure and activate the LAN interface for inter-VLAN routing. VLAN 99 is the native VLAN.
B1(config)# interface g0/0 B1(config-if)# no shutdown B1(config-if)# interface g0/0.10 B1(config-subif)# encapsulation dot1q 10 B1(config-subif)# ip address 10.1.10.1 255.255.255.0 B1(config-subif)# interface g0/0.20 B1(config-subif)# encapsulation dot1q 20 B1(config-subif)# ip address 10.1.20.1 255.255.255.0 B1(config-subif)# interface g0/0.30 B1(config-subif)# encapsulation dot1q 30 B1(config-subif)# ip address 10.1.30.1 255.255.255.0 B1(config-subif)# interface g0/0.99 B1(config-subif)# encapsulation dot1q 99 native B1(config-subif)# ip address 10.1.99.1 255.255.255.0
Static and Default Routing
- Configure HQ with a static route to the NewB LAN. Use the exit interface as an argument.
- Configure B1 with a default route to HQ. Use the next-hop IP address as an argument.
HQ(config)# ip route 10.4.5.0 255.255.255.0 serial 0/0/1 B1(config)# ip route 0.0.0.0 0.0.0.0 10.255.255.1
EIGRP Routing
- Configure and optimize HQ and B1 with EIGRP routing.
- Use autonomous system 100.
- Disable EIGRP updates on appropriate interfaces.
HQ(config)# router eigrp 100 HQ(config-router)# network 10.0.0.0 HQ(config-router)# passive-interface g0/0 HQ(config-router)# passive-interface s0/0/1
B1(config)# router eigrp 100 B1(config-router)# network 10.0.0.0 B1(config-router)# passive-interface g0/0.10 B1(config-router)# passive-interface g0/0.20 B1(config-router)# passive-interface g0/0.30 B1(config-router)# passive-interface g0/0.99
VLANs and Trunking Configurations
Note: Logging to the console is turned off on B1-S2 so that the Native VLAN mismatch messages will not interrupt your configurations. If you would prefer to view console messages, enter the global configuration command logging console.
- Configure trunking and VLANs on B1-S2.
- Create and name the VLANs listed in the VLAN Configuration and Port Mappings table on B1-S2 only.
- Configure the VLAN 99 interface and default gateway.
- Set trunking mode to on for F0/1 – F0/4.
- Assign VLANs to the appropriate access ports.
- Disable all unused ports and assign the BlackHole VLAN.
B1-S2(config)# vlan 10 B1-S2(config-vlan)# name Admin B1-S2(config-vlan)# vlan 20 B1-S2(config-vlan)# name Sales B1-S2(config-vlan)# vlan 30 B1-S2(config-vlan)# name Production B1-S2(config-vlan)# vlan 99 B1-S2(config-vlan)# name Mgmt&Native B1-S2(config-vlan)# vlan 999 B1-S2(config-vlan)# name BlackHole B1-S2(config)# interface vlan 99 B1-S2(config-if)# ip address 10.1.99.22 255.255.255.0 B1-S2(config-if)# exit B1-S2(config)# ip default-gateway 10.1.99.1 B1-S2(config)# interface range f0/1 - 4 B1-S2(config-if-range)# switchport mode trunk B1-S2(config-if-range)# switchport trunk native vlan 99 B1-S2(config-if-range)# exit B1-S2(config)# interface f0/6 B1-S2(config-if)# switchport mode access B1-S2(config-if)# switchport access vlan 10 B1-S2(config-if)# interface f0/11 B1-S2(config-if)# switchport mode access B1-S2(config-if)# switchport access vlan 20 B1-S2(config-if)# interface f0/16 B1-S2(config-if)# switchport mode access B1-S2(config-if)# switchport access vlan 30 B1-S2(config-if)# exit B1-S2(config)# interface range f0/5, f0/7-10, f0/12-15, f0/17-24, g0/1-2 B1-S2(config-if-range)# switchport access vlan 999 B1-S2(config-if-range)# shutdown
Port Security
- Use the following policy to establish port security on the B1-S2 access ports:
- Allow two MAC addresses to be learned on the port.
- Configure the learned MAC addresses to be added to the configuration.
- Set the port to send a message if there is a security violation. Traffic is still allowed from the first two MAC addresses learned.
B1-S2(config)# interface range f0/6, f0/11, f0/16 B1-S2(config-if-range)# switchport port-security B1-S2(config-if-range)# switchport port-security maximum 2 B1-S2(config-if-range)# switchport port-security mac-address sticky B1-S2(config-if-range)# switchport port-security violation restrict
SSH
- Configure HQ to use SSH for remote access.
- Set the modulus to 2048. The domain name is CCNASkills.com.
- The username is admin and the password is adminonly.
- Only SSH should be allowed on VTY lines.
- Modify the SSH defaults: version 2; 60-second timeout; two retries.
HQ(config)# ip domain-name CCNASkills.com HQ(config)# crypto key generate rsa HQ(config)# username admin password adminonly HQ(config)# line vty 0 4 HQ(config-line)# transport input ssh HQ(config-line)# login local HQ(config-line)# exit HQ(config)# ip ssh version 2 HQ(config)# ip ssh time-out 60 HQ(config)# ip ssh authentication-retries 2
DHCP
- On B1, configure a DHCP pool for the Sales VLAN 20 using the following requirements:
- Exclude the first 10 IP addresses in the range.
- The case-sensitive pool name is VLAN20.
- Include the DNS server attached to the HQ LAN as part of the DHCP configuration.
- Configure the Sales PC to use DHCP.
B1(config)# ip dhcp excluded-address 10.1.20.1 10.1.20.10 B1(config)# ip dhcp pool VLAN20 B1(dhcp-config)# network 10.1.20.0 255.255.255.0 B1(dhcp-config)# default-router 10.1.20.1 B1(dhcp-config)# dns-server 10.0.1.4
Click Sales PC > Desktop > IP Configuration
Change to DHCP and verify PC gets addressing information
Access List Policy
- Because HQ is connected to the Internet, configure and apply a named ACL called HQINBOUND in the following order:
- Allow inbound BGP updates (TCP port 179) for any source to any destination.
- Allow inbound HTTP requests from any source to the HQ-DataCenter network.
- Allow only established TCP sessions from the Internet.
- Allow only inbound ping replies from the Internet.
- Explicitly block all other inbound access from the Internet.
HQ(config)# ip access-list extended HQINBOUND HQ(config-ext-nacl)# permit tcp any any eq 179 HQ(config-ext-nacl)# permit tcp any 192.0.2.0 0.0.0.255 eq www HQ(config-ext-nacl)# permit tcp any any established HQ(config-ext-nacl)# permit icmp any any echo-reply HQ(config-ext-nacl)# deny ip any any HQ(config-ext-nacl)# exit HQ(config)# interface s0/1/0 HQ(config-if)# ip access-group HQINBOUND in
Connectivity
- Verify full connectivity from each PC to WWW.pka and www.cisco.pka.
- The Outside Host should be able to access the webpage at WWW.pka.
- All the test in Scenario 0 should be successful.
From year to year, Cisco has updated many versions with difference questions. The latest version is version 6.0 in 2018. What is your version? It depends on your instructor creating your class. We recommend you to go thought all version if you are not clear. While you take online test with netacad.com, You may get random questions from all version. Each version have 1 to 10 different questions or more. After you review all questions, You should practice with our online test system by go to "Online Test" link below.