Last Updated on July 15, 2015 by Admin
Cont.
Network communication does not happen without rules or protocols. In this class we will learn about the many protocols or rules that are necessary to send a message across the local area network as well as the internet. In order to have successful communication between people you have to follow social and cultural conventions, these are also called protocols.
For instance, if I go into a restaurant and walk past the hostess and right up to the waitress, while she is helping another table and demand some food; all the while not wearing a shirt, will I be successful? Probably not, because I am not following the convention of waiting to be seated, greeting the hostess, following her to a seat, getting my menu and so on and so forth. The rules for proper behavior for the restaurant system. Computer communication follows similar rules called protocols.
Protocols that allow computers to send and receive messages over networks are called network protocols. The protocols necessary for network communication are grouped together in stacks called protocol suites. These groups of protocols work together hierarchically which is commonly referred to as working in a layered architecture. Protocol suites are responsible for the format of the message which is a specific syntax, theprocess by which network devices will send information, reporting errors, and the beginning and termination of communication. Although protocols can be proprietary to one or more products or vendors they are often times written to comply with industry standards maintained by international committees like the IEEE. In this way protocols can be interoperable with many other devices, protocols and standards. Network protocols give the rules that govern communication, “the what” of what needs to happen in order to communicate, not “the how” of how that communication will be carried out. In this way, many different makers of computer hardware and technology can create there own products in their own way, as long as they adhere to the standardized rules of communication.
This is one of the examples of the benefits of a layered architecture, in that vendors do not have to write their own rules of communication, just adhere to the standards. Some of the benefits of using a layered architecture are: a common language to describe functions on specific layers, technology advancements on one layer does not effect the other layers (layer independence), specific layer requirements aid in the product design of how protocols interact with each other, interoperability allows for competition in the market.
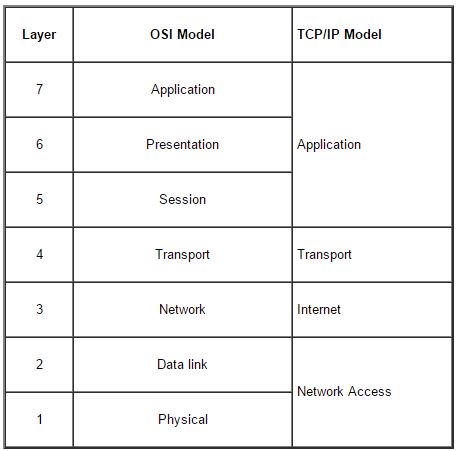
The two most well know networking models are the TCP/IP and the OSI models. The OSI or open systems interconnect model is the most widely recognized reference model for developing network protocols and applications. The OSI model was created as an open international standard but it was not adopted at as fast as the TCP/IP internet model and as a result the OSI model is purely an influential reference model which helps in the creation of other protocols and services. The TCP/IP model is the model of the internet and is based on the TCP/IP protocol suite. The TCP/IP model was widely adopted. Both models ultimately reflect analogous network layers that follow the similar functions.
The TCP/IP model has four layers but the Network Access Layer comprises the functions of both the Physical and Data Link layers in the OSI model. Similarly the Application layer of the TCP/IP model comprises the top three layers of the OSI model (Application, Presentation, and Session).
As data travels from a user’s computer (host) across the internet to another host the data is broken apart and built into “packets.” This process of building packets is calledencapsulation. Encapsulation happens from the top down starting with a user’s network application like a web browser, the data is broken into segments and the packet is built in descending layers down to the Physical layer. The packets then travel across the internet and at the receiving end the data built back together, called decapsulation, starting at layer one and moving up the layers until the data is completely rebuilt at the application layer and presented to the user.