Last Updated on October 18, 2019 by Admin
CCNA Cybersecurity Operations (Version 1.1) – CyberOps Chapter 2 Exam Answers 2019
-
What are two advantages of the NTFS file system compared with FAT32? (Choose two.)
- NTFS allows faster access to external peripherals such as a USB drive.
- NTFS supports larger files.
- NTFS provides more security features.
- NTFS allows faster formatting of drives.
- NTFS is easier to configure.
- NTFS allows the automatic detection of bad sectors.
Explanation: The file system has no control over the speed of access or formatting of drives, and the ease of configuration is not file system-dependent.
-
Where are the settings that are chosen during the installation process stored?
- in the recovery partition
- in BIOS
- in flash memory
- in the Registry
Explanation: The Registry contains all settings chosen from Control Panels, file associations, system policies, applications installed, and application license keys.
-
What technology was created to replace the BIOS program on modern personal computer motherboards?
- UEFI
- RAM
- CMOS
- MBR
Explanation: As of 2015, most personal computer motherboards are shipped with UEFI as the replacement for the BIOS program.
-
What term is used to describe a logical drive that can be formatted to store data?
- volume
- track
- sector
- cluster
- partition
Explanation: Hard disk drives are organized by several physical and logical structures. Partitions are logical portions of the disk that can be formatted to store data. Partitions consist of tracks, sectors, and clusters. Tracks are concentric rings on the disk surface. Tracks are divided into sectors and multiple sectors are combined logically to form clusters
-
Which two commands could be used to check if DNS name resolution is working properly on a Windows PC? (Choose two.)
- nslookup cisco.com
- net cisco.com
- ping cisco.com
- nbtstat cisco.com
- ipconfig /flushdns
Explanation: The ping command tests the connection between two hosts. When ping uses a host domain name to test the connection, the resolver on the PC will first perform the name resolution to query the DNS server for the IP address of the host. If the ping command is unable to resolve the domain name to an IP address, an error will result.
Nslookup is a tool for testing and troubleshooting DNS servers.
-
A technician is troubleshooting a PC unable to connect to the network. What command should be issued to check the IP address of the device?
- tracert
- ping
- nslookup
- ipconfig
Explanation: The commands tracert and ping are used to test the connectivity of the PC to the network. The command nslookup initiates a query to an Internet domain name server.
-
What utility is available on a Windows PC to view current running applications and processes?
- Task Manager
- Control Panel
- ipconfig
- nslookup
Explanation: On a Windows PC the Task Manager utility can be used to view the applications, processes, and services that are currently running.
-
A technician can ping the IP address of the web server of a remote company but cannot successfully ping the URL address of the same web server. Which software utility can the technician use to diagnose the problem?
- tracert
- ipconfig
- netstat
- nslookup
Explanation: Traceroute (tracert) is a utility that generates a list of hops that were successfully reached along the path from source to destination.This list can provide important verification and troubleshooting information. The ipconfig utility is used to display the IP configuration settings on a Windows PC. The Netstat utility is used to identify which active TCP connections are open and running on a networked host. Nslookup is a utility that allows the user to manually query the name servers to resolve a given host name. This utility can also be used to troubleshoot name resolution issues and to verify the current status of the name servers.
-
Which two things can be determined by using the ping command? (Choose two.)
- the number of routers between the source and destination device
- the IP address of the router nearest the destination device
- the average time it takes a packet to reach the destination and for the response to return to the source
- the destination device is reachable through the network
- the average time it takes each router in the path between source and destination to respond
Explanation: A ping command provides feedback on the time between when an echo request was sent to a remote host and when the echo reply was received. This can be a measure of network performance. A successful ping also indicates that the destination host was reachable through the network.
-
A user logs in to Windows with a regular user account and attempts to use an application that requires administrative privileges. What can the user do to successfully use the application?
- Right-click the application and choose Run as root.
- Right-click the application and choose Run as Priviledge.
- Right-click the application and choose Run as Superuser.
- Right-click the application and choose Run as Administrator.
Explanation: As a security best practice, it is advisable not to log on to Windows using the Administrator account or an account with administrative privileges. When it is necessary to run or install software that requires the privileges of the Administrator, the user can right-click the software in the Windows File Explorer and choose Run as Administrator.
-
Which two user accounts are automatically created when a user installs Windows to a new computer? (Choose two.)
- root
- guest
- system
- superuser
- administrator
Explanation: When a user installs Windows, two local user accounts are created automatically during the process, administrator and guest.
-
Which type of Windows PowerShell command performs an action and returns an output or object to the next command that will be executed?
- scripts
- cmdlets
- routines
- functions
Explanation: The types of commands that PowerShell can execute include the following:cmdlets – perform an action and return an output or object to the next command that will be executed
PowerShell scripts – files with a .ps1 extension that contain PowerShell commands that are executed
PowerShell functions – pieces of code that can be referenced in a script
-
What is the purpose of using the net accounts command in Windows?
- to start a network service
- to display information about shared network resources
- to show a list of computers and network devices on the network
- to review the settings of password and logon requirements for users
Explanation: These are some common net commands:
net accounts – sets password and logon requirements for users
net start – starts a network service or lists running network services
net use – connects, disconnects, and displays information about shared network resources
net view – shows a list of computers and network devices on the network
When used without options, the net accounts command displays the current settings for password, logon limitations, and domain information.
-
What is the purpose of entering the netsh command on a Windows PC?
- to create user accounts
- to test the hardware devices on the PC
- to change the computer name for the PC
- to configure networking parameters for the PC
Explanation: The netsh.exe tool can be used to configure networking parameters for the PC from a command prompt.
-
What are two reasons for entering the ping 127.0.0.1 command on a Windows PC? (Choose two.)
- to check if the NIC functions as expected
- to ensure that the PC can connect to remote networks
- to check if the default gateway is configured correctly
- to check if the TCP/IP protocol suite is installed properly
- to display the bandwidth and throughput of the network connection
Explanation: The IP address 127.0.0.1 is a loopback address on the PC. A successful ping to the loopback address indicates that the TCP/IP protocol suite is installed properly and the NIC is working as expected. A ping to the loopback address does not test the connectivity to remote networks, nor will it display bandwidth and throughput information.
-
What are two reasons for entering the ipconfig command on a Windows PC? (Choose two.)
- to review the status of network media connections
- to check if the DNS server can be contacted
- to review the network configuration on the PC
- to ensure that the PC can connect to remote networks
- to display the bandwidth and throughput of the network connection
Explanation: The command ipconfig is a useful tool for troubleshooting. The command will display some IP addressing configuration and the network media connection status. The command does not test the connection to the DNS server configured or test remote networks. It does not display bandwidth and throughput information.
-
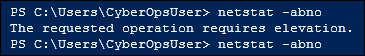
Refer to the exhibit. A cyber security administrator is attempting to view system information from the Windows PowerShell and recieves the error message shown. What action does the administrator need to take to successfully run the command?
- Run the command from the command prompt.
- Restart the abno service in Task Manager.
- Install latest Windows updates.
- Run PowerShell as administrator.
Explanation: Best practices advise not to log into systems with an administrator account, but rather a user account. When logged in as a user it is possible to run Windows utilitites, such as PowerShell and the Command Prompt as an administrator by right clicking on the utility and slecting Run as Administrator.
-
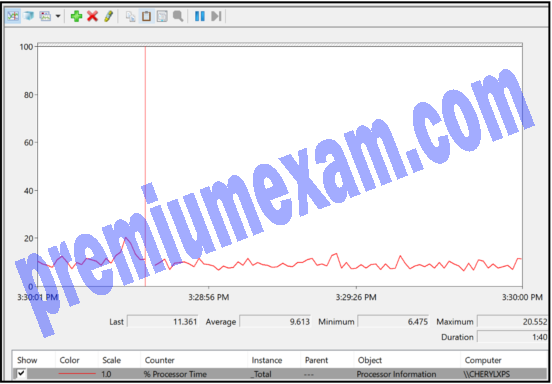
Refer to the exhibit. Which Microsoft Windows application is being used?
- Performance Monitor
- PowerShell
- Event Viewer
- Task Manager
Explanation: Windows Performance Monitor is used to evaluate the performance of individual components on a Windows host computer. Commonly monitored components include the processor, hard drive, network, and memory. Windows Task Manager and Performance Monitor are used when malware is suspected and a component is not performing the way it should.
-
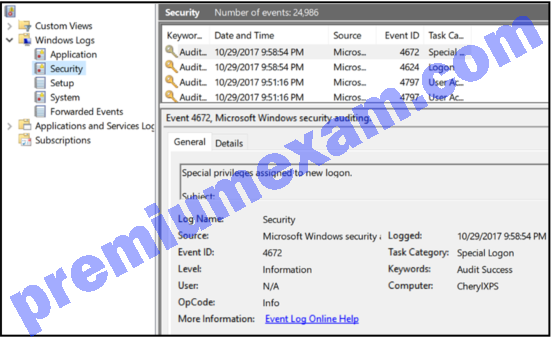
Refer to the exhibit. A cybersecurity analyst is investigating a reported security incident on a Microsoft Windows computer. Which tool is the analyst using?
- Event Viewer
- Performance Monitor
- PowerShell
- Task Manager
Explanation: Event Viewer is used to investigate the history of application, security, and system events. Events show the date and time that the event occurred along with the source of the event. If a cybersecurity analyst has the address of the Windows computer targeted and/or the date and time that a security breach occurred, the analyst could use Event Viewer to document and prove what occurred on the computer.
-
Consider the path representation in Windows CLI C:\Users\Jason\Desktop\mydocu.txt. What does the Users\Jason component represent?
- storage device or partition
- file attribute
- file directory and subdirectory
- current file directory
Explanation: In the path representation in Windows CLI, the components of C:\Users\Jason\Desktop\mydocu.txt are as follows:C:\ represents the root directory of the storage device.
Users\Jason represents the file directory.
Desktop represents the current file directory.
The mydocu.txt represents the user file.
-
For security reasons a network administrator needs to ensure that local computers cannot ping each other. Which settings can accomplish this task?
- smartcard settings
- firewall settings
- MAC address settings
- file system settings
Explanation: Smartcard and file system settings do not affect network operation. MAC address settings and filtering may be used to control device network access but cannot be used to filter different data traffic types.
-
What would be displayed if the netstat -abno command was entered on a Windows PC?
- a local routing table
- only active TCP connections in an ESTABLISHED state
- only active UDP connections in an LISTENING state
- all active TCP and UDP connections, their current state, and their associated process ID (PID)
Explanation: With the optional switch -abno, the netstat command will display all network connections together with associated running processes. It helps a user identify possible malware connections.
-
What function is provided by the Windows Task Manager?
- It provides information on system resources and processes.
- It maintains system logs.
- It selectively denies traffic on specified interfaces.
- It provides an active list of TCP connections.
Explanation: Windows Task Manager enables an end user to monitor applications, processes, and services currently running on the end device. It can be used to start or stop programs, stop processes, and display informative statistics about the device.
-
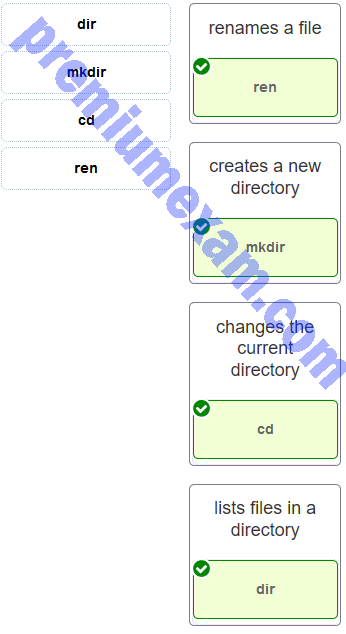
Match the Windows command to the description.
-
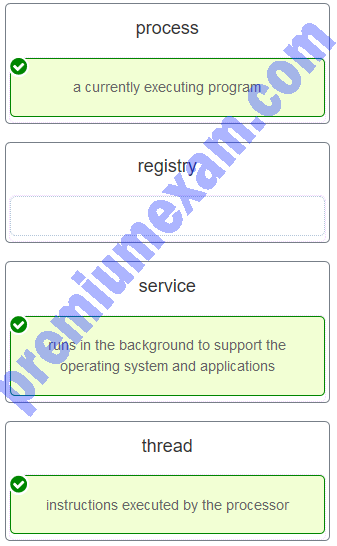
Match the definition to the Microsoft Windows term. (Not all options are used.)
-
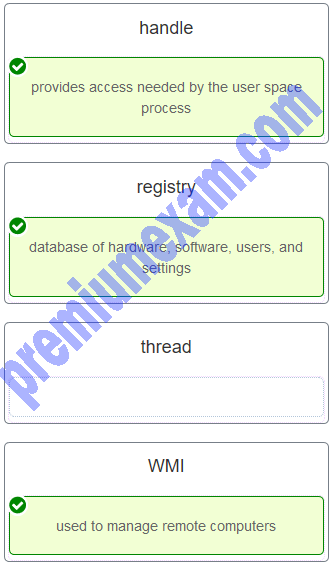
Match the Windows term to the description.
-
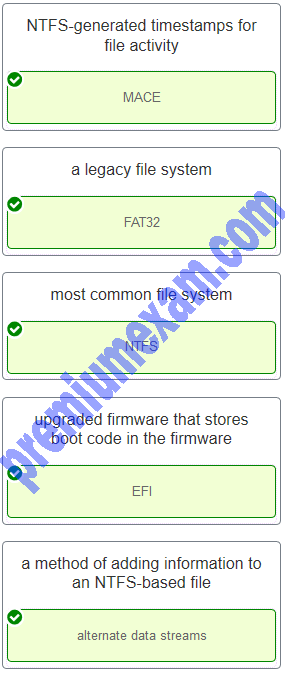
Match the definition to the Microsoft Windows term. (Not all options are used.)