Last Updated on October 18, 2019 by Admin
CCNA Cybersecurity Operations (Version 1.1) – CyberOps Chapter 1 Exam Answers 2019 Full 100%
-
What was used as a cyberwarfare weapon to attack a uranium enrichment facility in Iran?
- DDoS
- PSYOPS
- SQL injection
- Stuxnet
Explanation: The Stuxnet malware program is an excellent example of a sophisticated cyberwarfare weapon. In 2010, it was used to attack programmable logic controllers that operated uranium enrichment centrifuges in Iran.
-
What is a potential risk when using a free and open wireless hotspot in a public location?
- Network traffic might be
- hijacked and information stolen.
- Too many users trying to connect to the Internet may cause a network traffic jam.
- The Internet connection can become too slow when many users access the wireless hotspot.
- Purchase of products from vendors might be required in exchange for the Internet access.
Explanation: Many free and open wireless hotspots operate with no authentication or weak authentication mechanisms. Attackers could easily capture the network traffic in and out of such a hotspot and steal user information. In addition, attackers might set up a “rogue” wireless hotspot to attract unsuspecting users to it and then collect information from those users.
-
Which two services are provided by security operations centers? (Choose two.)
- monitoring network security threats
- responding to data center physical break-ins
- providing secure Internet connections
- managing comprehensive threat solutions
- ensuring secure routing packet exchanges
Explanation: Security operations centers (SOCs) can provide a broad range of services to defend against threats to information systems of an organization. These services include monitoring threats to network security and managing comprehensive solutions to fight against threats. Ensuring secure routing exchanges and providing secure Internet connections are tasks typically performed by a network operations center (NOC). Responding to facility break-ins is typically the function and responsibility of the local police department.
-
Which statement describes cyberwarfare?
- Cyberwarfare is an attack carried out by a group of script kiddies.
- It is simulation software for Air Force pilots that allows them to practice under a simulated war scenario.
- It is a series of personal protective equipment developed for soldiers involved in nuclear war.
- It is Internet-based conflict that involves the penetration of information systems of other nations.
Explanation: Cyberwarfare is Internet-based conflict that involves the penetration of the networks and computer systems of other nations. Organized hackers are typically involved in such an attack.
-
Which personnel in a SOC are assigned the task of hunting for potential threats and implementing threat detection tools?
- SOC Manager
- Tier 1 Analyst
- Tier 2 Incident Reporter
- Tier 3 SME
Explanation: In a SOC, Tier 3 SMEs have expert-level skills in network, endpoint, threat intelligence, and malware reverse engineering (RE). They are deeply involved in hunting for potential security threats and implementing threat detection tools.
-
In the operation of a SOC, which system is frequently used to let an analyst select alerts from a pool to investigate?
- syslog server
- ticketing system
- registration system
- security alert knowledge-based system
Explanation: In a SOC, a ticketing system is typically used for a work flow management system.
-
Why do IoT devices pose a greater risk than other computing devices on a network?
- Most IoT devices do not require an Internet connection and are unable to receive new updates.
- IoT devices require unencrypted wireless connections.
- IoT devices cannot function on an isolated network with only an Internet connection.
- Most IoT devices do not receive frequent firmware updates.
Explanation: IoT devices commonly operate using their original firmware and do not receive updates as frequently as laptops, desktops, and mobile platforms.
-
Which personnel in a SOC is assigned the task of verifying whether an alert triggered by monitoring software represents a true security incident?
- SOC Manager
- Tier 1 personnel
- Tier 2 personnel
- Tier 3 personnel
Explanation: In a SOC, the job of a Tier 1 Alert Analyst includes monitoring incoming alerts and verifying that a true security incident has occurred.
-
Which three technologies should be included in a SOC security information and event management system? (Choose three.)
- proxy service
- log management
- firewall appliance
- threat intelligence
- security monitoring
- intrusion prevention
Explanation: Technologies in a SOC should include the following:
Event collection, correlation, and analysis
Security monitoring
Security control
Log management
Vulnerability assessment
Vulnerability tracking
Threat intelligence
Proxy server, VPN, and IPS are security devices deployed in the network infrastructure.
-
If a SOC has a goal of 99.999% uptime, how many minutes of downtime a year would be considered within its goal?
- Approximately 5 minutes per year.
- Approximately 10 minutes per year.
- Approximately 20 minutes per year.
- Approximately 30 minutes per year.
Explanation: Within a year, there are 365 days x 24 hours a day x 60 minutes per hour = 525,600 minutes. With the goal of uptime 99.999% of time, the downtime needs to be controlled under 525,600 x (1-0.99999) = 5.256 minutes a year.
-
Which statement best describes a motivation of hacktivists?
- They are trying to show off their hacking skills.
- They are curious and learning hacking skills.
- They are part of a protest group behind a political cause.
- They are interested in discovering new exploits.
Explanation: Each type of cybercriminal has a distinct motivation for his or her actions.
-
How does a security information and event management system (SIEM) in a SOC help the personnel fight against security threats?
- by analyzing logging data in real time
- by dynamically implementing firewall rules
- by combining data from multiple technologies
- by integrating all security devices and appliances in an organization
Explanation: A security information and event management system (SIEM) combines data from multiple sources to help SOC personnel collect and filter data, detect and classify threats, analyze and investigate threats, and manage resources to implement preventive measures.
-
What name is given to an amateur hacker?
- black hat
- red hat
- script kiddie
- blue team
Explanation: Script kiddies is a term used to describe inexperienced hackers.
-
Which organization offers the vendor-neutral CySA+ certification?
- IEEE
- GIAC
- (ISC)²
- CompTIA
Explanation: The CompTIA Cybersecurity Analyst (CySA+) certification is a vendor-neutral security professional certification.
-
Users report that a database file on the main server cannot be accessed. A database administrator verifies the issue and notices that the database file is now encrypted. The organization receives a threatening email demanding payment for the decryption of the database file. What type of attack has the organization experienced?
- DoS attack
- man-in-the-middle attack
- ransomware
- Trojan horse
Explanation: A cybersecurity specialist needs to be familiar with the characteristics of the different types of malware and attacks that threaten an organization.
-
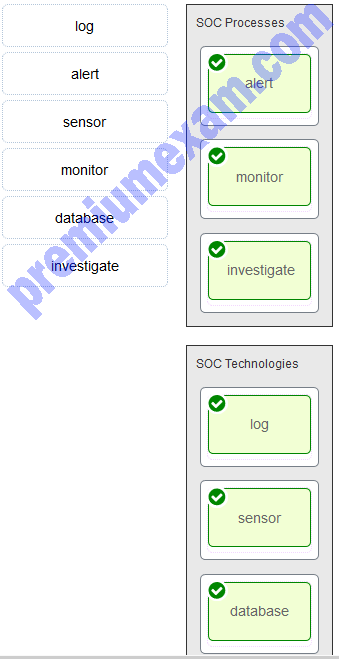
Match the components to the major categories in a SOC.