Last Updated on January 28, 2021 by Admin
Networking Essentials Practice Final Exam Answers Full 100% 2019
-
What is the reason that electronic data is represented as bits in computer processing and data communication?
- Bits are the format best understood by people.
- Bits are more secure and make transmissions harder to hack.
- Bits are more efficient for storing data.
- Bits decrease the number of connections that need to be made.
Explanation: In electronic communication, data is represented by 1’s and 0’s. These 1’s and 0’s are referred to as binary digits. This format is identified as digital binary. All electronic data is stored in this binary format because it can be stored more efficiently and can be transmitted over longer distances without the quality becoming degraded.
-
Which term is used to describe a network device that relies on another device to obtain information?
- web server
- console
- server
- client
Explanation: A client device has software installed which enables it to request the required service from a server device. For instance, a user who uses a web browser is effectively requesting pages from servers all over the web. In this case the browser is considered the client, whereas the device that is responsible for answering the request is considered the server.
-
What is a role of an intermediary device on a network?
- functions as the primary source of information for end devices
- determines the path and directs data along the way to its final destination
- runs applications that support collaboration for business
- forms the interface between the human network and the underlying communication network
Explanation: Processes running on the intermediary network devices perform functions like regenerating and re-transmitting data signals, maintaining information about what pathways exist through the network and internetwork, directing data along alternate pathways when there is a link failure, and permitting or denying the flow of data, based on security settings.
-
Which type of network component can be used to share an attached printer to the network?
- personal computer
- peripheral
- access point
- network media
Explanation: A peripheral is a device that is not directly connected to a network. In order to be made available on a network, a host is responsible for sharing the peripheral across the network.
-
Which two devices are shared peripherals? (Choose two.)
- tablet
- laptop
- scanner
- printer
- touch-pad with digital stylus
Explanation: A shared peripheral device does not connect directly to a network. This device is attached to a host (such as a PC) and the host connects to the network to share the peripheral device.
-
When troubleshooting network problems, where would a network administrator find the configuration information, such as the computer names and the IP addresses that are used?
- physical topology diagram
- DHCP server
- DNS server
- logical topology diagram
Explanation: A logical topology usually contains relevant network configuration information, such as the following:
- Device names
- Device IP addressing
- Network designations
- Configuration information
-
When is a straight-through cable used in a network?
- when connecting a host to another host
- when connecting a host to a router
- when connecting a host to a switch
- when connecting a router to another router
Explanation: When two unlike devices are connected, they require a straight-through cable to exchange data. When two like devices are connected together, they require the use of a crossover cable in order to reverse the transmit and receive functions so they can exchange data.
-
Which organization publishes and manages the Request for Comments (RFC) documents?
- IEEE
- ISO
- IETF
- TIA/EIA
Explanation: The Internet Engineering Task Force (IETF) organization publishes and manages the Request for Comments (RFC).
-
What is indicated by the 100 in the 100BASE-T standard?
- meters
- feet
- megabits per second
- twists per meter
Explanation: 100BASE-T is an Ethernet standard that translates to 100 megabits per second, baseband transmission, and twisted pair cable.
-
What is the default subnet mask for an IP address of 198.133.219.4?
- 255.0.0.0
- 255.255.0.0
- 255.255.255.0
- 255.255.255.255
Explanation: In classful IPv4 addressing, a network with the first octet of 198 is a Class C network with the default subnet mask of 255.255.255.0.
-
What are three characteristics of multicast transmission? (Choose three.)
- The source address of a multicast transmission is in the range of 224.0.0.0 to 224.0.0.255.
- A single packet can be sent to a group of hosts.
- Multicast transmission can be used by routers to exchange routing information.
- Routers will not forward multicast addresses in the range of 224.0.0.0 to 224.0.0.255.
- Computers use multicast transmission to request IPv4 addresses.
- Multicast messages map lower layer addresses to upper layer addresses.
Explanation: Broadcast messages consist of single packets that are sent to all hosts on a network segment. These types of messages are used to request IPv4 addresses, and map upper layer addresses to lower layer addresses. A multicast transmission is a single packet sent to a group of hosts and is used by routing protocols, such as OSPF and RIPv2, to exchange routes. The address range 224.0.0.0 to 224.0.0.255 is reserved for link-local addresses to reach multicast groups on a local network.
-
A client device on an Ethernet segment needs an IP address in order to communicate on the network. A DHCP server with IP address 192.168.1.1 has been configured and enabled on the network. How will a client device obtain a usable IP address for this network?
- Send a DHCPREQUEST packet to IP address 255.255.255.255.
- Send a DHCPACK packet to the default gateway address.
- Send a DHCPDISCOVER message to physical address FF-FF-FF-FF-FF-FF.
- Use a statically configured IP address from the pool of IP addresses that is offered by the DHCP server.
Explanation: Like IP addressing, there is also a special MAC address for broadcast purposes: FF-FF-FF-FF-FF-FF. When a DHCP client needs to send a DHCP Discover message in order to seek DHCP servers, the client will use this MAC address as the destination MAC address in the Ethernet frame. It does this because it has no knowledge of the IP and MAC addresses of DHCP servers.
-
Which number grouping is a valid IPv6 address?
- 1234:1230::1238::1299:1000::
- 12aa::1298:1200::129b
- 1b10::1100::2001::2900::ab11::1102::0000::2900
- 2001:0db8:3c55:0015:1010:0000:abcd:ff13
Explanation: An IPv6 address is made up of 128 bits represented in hexadecimal numbers.There are two rules that help reduce the number of digits needed to represent an IPv6 address.
- Rule 1 – Omit leading zeros in any 16-bit section.
- Rule 2 – Replace any single group of consecutive zeros with a double colon (::). This can only be used once within an IPv6 address.
-
Which protocol operates at the transport layer of the TCP/IP model and ensures reliable delivery of IP packets?
- HTTP
- IP
- UDP
- TCP
Explanation: Transmission Control Protocol (TCP) operates at the transport layer of the TCP/IP model. TCP ensures that IP packets are delivered reliably.
-
Which term is used to describe transport layer ports in the range of 1 through 1023?
- private
- well-known
- registered
- source
Explanation: Port numbers are addressed at the transport layer of the OSI model by TCP and UDP to identify requested protocols and services. Port numbers in the range of 1 to 1023 are well-known ports.
-
What is a function of a DNS server?
- It determines the IP address that is associated with a specific host domain name.
- It maps IP addresses to physical addresses.
- It translates private IP addresses to public IP addresses.
- It assigns logical address information to host computers.
Explanation: Hosts are assigned with IP addresses in order to communicate over the network. Hosts are registered with domain names so people can remember and recognize them easily. However, computers are connected through their IP addresses. DNS provides the service to map the domain name to its IP address.
-
What are two benefits of wireless networks over wired networks? (Choose two.)
- anytime, anywhere connectivity
- immunity to interference
- increased security
- mobility
- speed
Explanation: Benefits of wireless technology include the following:
- Mobility – easy device connectivity
- Flexibility – anytime, anywhere connectivity
- Scalability – easily expanded
- Cost savings – equipment costs continue to drop
- Quick installation – does not take long to install and provides connectivity for quite a range
- Reliability – even in harsh environments, wireless can be easy to install in emergency or hostile environments
-
Which type of network is covered by the IEEE 802.11 standards?
- Internet
- WAN
- Wi-Fi
- Ethernet
Explanation: IEEE 802.11 wireless standards use the 2.4 and 5 GHz unregulated frequency ranges.
-
When a wireless router is being configured for the first time, what type of wired connection is used?
- console cable
- Ethernet patch cable
- modem cable
- telephone cable
Explanation: A straight-through Ethernet cable, or patch cable, is commonly used to connect to a wireless router for initial configuration.
-
Which is an example of social engineering?
- a computer displaying unauthorized pop-ups and adware
- the infection of a computer by a virus carried by a Trojan
- an anonymous programmer directing a DDoS attack on a data center
- an unidentified person claiming to be a technician collecting user information from employees
Explanation: A social engineer attempts to gain the confidence of an employee and convince that person to divulge confidential and sensitive information, such as usernames and passwords. DDoS attacks, pop-ups, and viruses are all examples of software based security threats, not social engineering.
-
Which malicious program appears as a legitimate program to deceive the victim, but is in fact an attack tool that can contain malicious code?
- Trojan horse
- worm
- virus
- spyware
Explanation: A Trojan horse is a malicious program that appears legitimate but actually carries code which can damage computer systems or install backdoors if the program is initiated.
-
A file is downloaded from the Internet. After the user opens the downloaded file, the hard drive crashes and all information on the computer is lost. What type of attack occurred?
- worm
- virus
- Trojan horse
- denial of service
Explanation: Viruses are malicious programs that are spread by modifying other programs and files and can cause hard drives to crash and files to be lost.
-
What is required for a network administrator to perform out-of-band management tasks on a Cisco device?
- a valid IP address configured on VLAN 1
- SSH enabled and functional on the device
- an active network connection available to the device
- a computer directly connected to the console port of the device
Explanation: With out-of-band management, the only requirement is to have a computer directly connected to the console port of the device. This is the primary method to configure a new device because no network connection or prior configurations on the device is required.
-
What are two options for expanding storage space on a Cisco router? (Choose two.)
- RAM
- ROM
- NVRAM
- flash slots
- USB ports
Explanation: ROM and RAM are memory modules built into a Cisco device and their capacity does not change. In a Cisco 1941 router, two flash slots and two USB ports are included that expand the storage capability and flexibility. NVRAM is a type of memory that is used to store a backup of the configuration file.
-
If the default gateway is configured incorrectly on a host, what is the impact on communications?
- The host is unable to communicate on the local network.
- The host is unable to communicate with hosts on remote networks.
- The host is unable to communicate with hosts on both the local and remote networks.
- The host cannot get an IP address from the DHCP server.
Explanation: In data communication, the default gateway device is involved only when a host needs to communicate with other hosts on another network. The default gateway address identifies a network device that a host device uses to communicate with devices on other networks. The default gateway device is not used when a host communicates with other hosts on the same network.
-
A user calls the help desk to report a workstation problem. Which three questions would produce the most helpful information for troubleshooting? (Choose three.)
- If you received an error message, what was it?
- What changes have you made to your workstation?
- Do you have the warranty for your workstation?
- What operating system version is running on your workstation?
- Have you used a network monitoring tool on your workstation?
- Have you performed a backup recently?
Explanation: In troubleshooting, the first step is to gather information related to the problem. One way to gather information is to ask questions of the individual who reported the problem as well as any other affected users. Questions should include end user experiences, observed symptoms, error messages, and information about recent configuration changes to devices or applications.
-
Which command can be used to verify connectivity between two host devices?
- ipconfig
- ping
- netstat
- nslookup
Explanation: The ping command can be used to test end-to-end connectivity between two host devices. It measures the round-trip time for a message to get from source to destination.
-
Users are complaining that they are unable to browse certain websites on the Internet. An administrator can successfully ping a web server via its IP address, but cannot browse to the domain name of the website. Which troubleshooting tool would be most useful in determining where the problem is?
- netstat
- tracert
- nslookup
- ipconfig
Explanation: The nslookup command can be used to look up information about a particular DNS name in the DNS server. The information includes the IP address of the DNS server being used as well as the IP address associated with the specified DNS name. This command can help verify the DNS that is used and if the domain name to IP address resolution works.
-
Which utility can be used to view a list of open TCP connections on Linux or Windows systems?
- Tracert
- Ping
- Netstat
- Ipconfig
Explanation: Netstat is a utility that is available for both Linux and Windows systems. It is a utility that can be used to indicate that something or someone is connected to the local host. It lists the protocol in use, the local address and port numbers, the foreign address and port numbers, and the state of the connection.
-
Refer to the exhibit. The command output is from a wireless DHCP host connected to a Linksys integrated router. What can be determined from the output?
- There is a DNS problem.
- A new wireless NIC needs to be installed.
- The DHCP configuration needs to be checked.
- The connection to the SSID needs to be verified.
- An incorrect cable is being used between the host and the router.
Explanation: The default gateway IP address must be in the same network as the host in order for the host and router to communicate with each other. Because this is a DHCP client, the IP configuration is provided by the DHCP. Thus the DHCP configuration should be checked and corrected.
-
Fill in the blank.
When a Cisco device is powered on, the POST begins to test the device and determine if it is functioning properly.
-
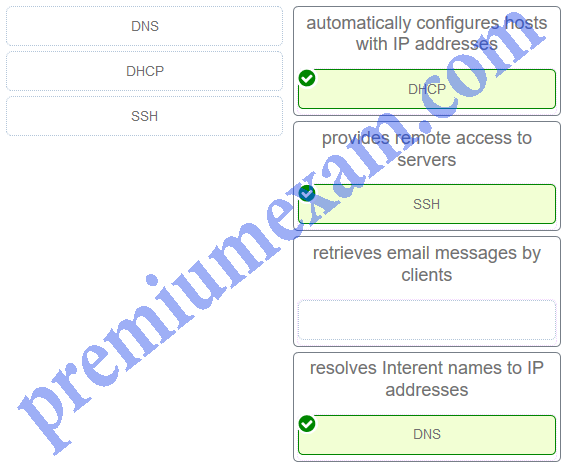
Match the protocol with the function. (Not all options are used.)
-
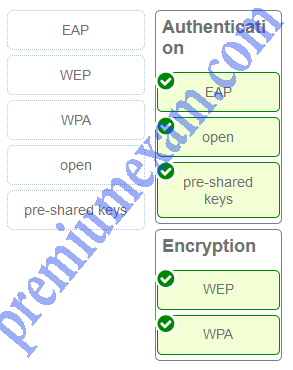
Match the term to the category.
-
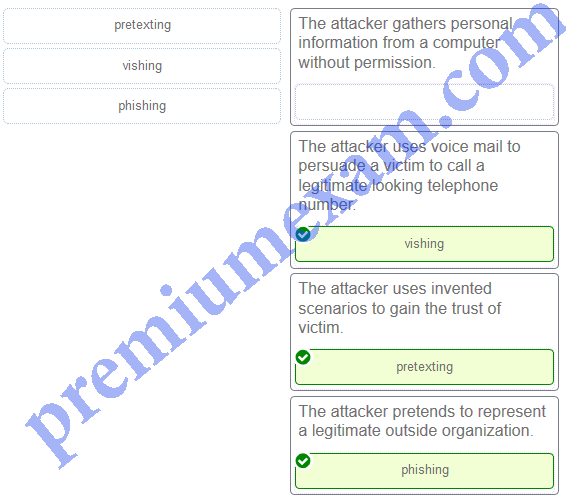
Match the type of attack with the description. (Not all options are used.)
-
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
What is the phrase displayed on the webpage?
- Correctly done.
- Configuration is successful.
- Your configuration is correct.
- You have configured the devices right.
Explanation: In order for the wireless clients in the internal network to reach the Internet, the border router and the wireless router must be configured according to the network design parameters.