Last Updated on February 1, 2021 by Admin
CCNA3 v7 – ENSA – CCNA (200-301) – CCNA Certification Practice Exam Answers Full 100% 2020
Cisco Netacad ENSA Version 7.00 CCNA 3 v7 ENSA – CCNA Certification Practice Exam Answers 2020 2021 – Enterprise Networking, Security, and Automation
-
What characteristic completes the following statement?
When an IPv6 static route is configured, and traffic is to be directed to one specific server, the static route requires ……
- the “show ipv6 route static” command.
- the interface type and interface number.
- a destination host route with a /128 prefix.
- an administrative distance of 2.
-
What term describes a default queuing method where packets are sent out of an interface in the order in which they arrive?
- traffic shaping
- low latency queuing (LLQ)
- weighted random early detection (WRED)
- weighted fair queuing (WFQ)
- first-in, first-out (FIFO)
-
Which LAN attack enables traffic from one VLAN to be seen by another VLAN without the aid of a router?
- VLAN hopping attack
- DHCP spoofing attack
- DHCP starvation attack
- VLAN double-tagging attack
-
A network engineer is designing a borderless switched network in a hierarchical fashion. Which guideline might cause the engineer to implement a three-tier layer model?
- The core layer provides differentiated services to various classes of service applications at the edge of the network.
- Fault isolation is one of the primary purposes of the distribution layer.
- Access layer L2 switches connect to distribution layer L3 switches, which implement routing, quality of service, and security.
- The access layer provides aggregation of Layer 2 broadcast domains.
-
A group of network technicians is discussing IPv6 multicast processes. What is a feature of one type of IPv6 multicast address that should be discussed?
- It has the prefix fe00::/8.
- A solicited-node multicast address is similar to the all-routers multicast address.
- It can be a source or a destination address.
- The all-nodes multicast group has the same effect as an IPv4 broadcast address.
-
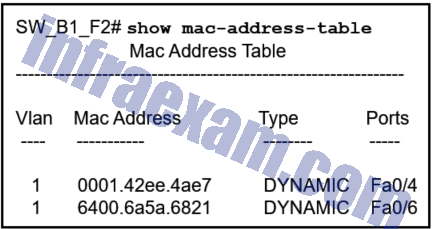
Refer to the exhibit. A PC with the MAC address of 0800.069d.3841 attached to port Fa0/8 is sending data to a device that has the MAC address of 6400.6a5a.6821. What will the switch do first to handle the data transfer?
- The switch will send the frame to ports Fa0/4 and Fa0/6.
- The switch will add the address 0800.069d.3841 to the MAC address table.
- The switch will flood the frame out all ports except port Fa0/8.
- The switch will send the frame to port Fa0/6.
- The switch will add the address 6400.6151.6821 to the MAC address table.
Answers Explanation & Hints: Every frame that enters a switch is checked for new information to learn. It does this by examining the source MAC address of the frame and port number where the frame entered the switch:
If the source MAC address does not exist in the MAC address table, the MAC address and incoming port number are added to the table.
-
A technician needs to add a new wireless device to a small WLAN. The WLAN is a mixture of old and newer 802.11b and 802.11g devices. What choice for the new device would provide the most interoperability for present and future growth?
- Add a new 802.11b device.
- Add a new 802.11n device.
- Add a new 802.11g device.
- Add a new 802.11a device.
-
What are two benefits of using virtualization? (Choose two.)
- The performance of a virtual machine is faster than the performance of the operating system running on physical hardware.
- The virtual machine is no longer dependent on a specific hardware platform.
- Because all virtual operating systems are contained within a single virtual network, networking connections are simplified.
- Multiple virtual machines can be running simultaneously on a single physical device.
- The operating system of the virtual machine does not require licensing when it is virtualized.
-
An administrator needs to implement a 2.4GHz WLAN that requires multiple APs. Which two are characteristics of the 2.4GHz channels? (Choose two.)
- Each channel is separated from the next channel by 20 MHz.
- Each channel is allotted 22 MHz bandwidth.
- There are 11 channels for North America identified by the 802.11b standard.
- If three adjacent APs are required, the non-overlapping channels 1, 21, and 41 are recommended.
- They can provide faster data transmission for wireless clients in heavily populated wireless networks than 5GHz channels.
-
A pharmaceutical company wants to contract the services of a cloud provider to store employee data and company-specific applications with strict access security. Which type of cloud would be the most appropriate for this scenario?
- private cloud
- community cloud
- hybrid cloud
- public cloud
Answers Explanation & Hints: Private clouds – Cloud-based applications and services offered in a private cloud are intended for a specific organization or entity, such as the government. A private cloud can be set up using the organization’s private network, though this can be expensive to build and maintain. A private cloud can also be managed by an outside organization with strict access security.
-
Which feature or function does an AP provide in a wireless LAN?
- An AP is easier to configure and to set up than Wi-Fi range extenders.
- A wireless device has to be associated to an AP in order to have access to network resources.
- Each AP advertises one or more SSIDs and a user can choose to connect to the closest SSID.
- A wireless client can connect to more than one AP at a time.
-
What is a difference between autonomous APs and controller-based APs in wireless LANs?
- Controller-based APs support PAgP and LACP protocols, whereas autonomous APs do not.
- Autonomous APs require no initial configuration, whereas the lightweight APs require an initial configuration before communicating with a WLAN controller.
- Autonomous APs are easier to configure and manage than are controller-based APs.
- When wireless demands increase, controller-based APs provide a better solution than do autonomous APs.
-
A technician is reviewing a report of slowness during peak traffic periods and is looking at performance on a particular switch. What should the technician be aware of about memory buffering on a switch?
- Shared memory allows traffic received on one port to be transmitted to another port without moving the data to a different queue.
- The amount of buffer memory required by a port is dynamically allocated when port-based memory is used.
- If shared memory is used, a single frame can delay the transmission of all others in memory because of a busy destination port.
- The port-based memory method is more appropriate to asymmetric switching.
-
A network engineer is designing a borderless switched network in a hierarchical fashion. Why might the engineer consider using a two-tier layer model?
- It is recommended in smaller campus locations where there are fewer users accessing the network.
- It consists of a collapsed layer composed of the access and the distribution layer, and a second layer composed of the core layer.
- The access layer in this model has different functions from the access layer in the three-tier layer model.
- The primary function of the collapsed layer is to provide network access to the user.
-
A network engineer is configuring a Cisco router as a DHCP relay. When issuing the ip helper-address command in the interface configuration mode which IPv4 address is added to the command?
- DHCPv4 subnet address
- DHCPv4 server address
- DHCPv4 client default gateway address
- DHCPv4 client address
-
A network engineer is configuring secure remote access to a Cisco router. Which two commands would be issued in the line configuration mode of the router to implement SSH? (Choose two.)
- username admin secret ccna
- ip ssh version 2
- login local
- transport input ssh
- crypto key generate rsa
-
What is the purpose of the overload keyword in the ip nat inside source list 1 pool NAT_POOL overload command?
- It allows a list of internal hosts to communicate with a specific group of external hosts.
- It allows external hosts to initiate sessions with internal hosts.
- It allows many inside hosts to share one or a few inside global addresses.
- It allows a pool of inside global addresses to be used by internal hosts.
Answers Explanation & Hints: Dynamic NAT uses a pool of inside global addresses that are assigned to outgoing sessions. If there are more internal hosts than public addresses in the pool, then an administrator can enable port address translation with the addition of the overload keyword. With port address translation, many internal hosts can share a single inside global address because the NAT device will track the individual sessions by Layer 4 port number.
-
Which is a QoS model that a network engineer would implement to ensure a source to destination quality of service standard for a specified data flow?
- integrated services
- best effort
- class-based weighted fair queuing
- differentiated services
- low latency queuing
-
When an end device requests services from a DHCPv4 server it receives a host IPv4 address and a subnet mask. Which two other IPv4 addresses are also typically provided to a DCHPv4 client? (Choose two.)
- DNS server address
- automatic private IPv4 address
- local HTTP web server address
- LAN default gateway address
- LAN NTP server address
-
Which type of API would be used to allow authorized salespeople of an organization access to internal sales data from their mobile devices?
- public
- partner
- private
- open
-
What are two syntax rules for writing a JSON array? (Choose two.)
- A semicolon separates the key and list of values.
- Each value in the array is separated by a comma.
- The array can include only one value type.
- Values are enclosed in square brackets.
- A space must separate each value in the array.
-
What are three components used in the query portion of a typical RESTful API request? (Choose three.)
- protocol
- API server
- format
- resources
- key
- parameters
-
What is a characteristic of the REST API?
- most widely used API for web services
- evolved into what became SOAP
- used for exchanging XML structured information over HTTP or SMTP
- considered slow, complex, and rigid
-
A network administrator is using the Cisco DNA Center to monitor network health and to troubleshoot network issues. Which area should the administrator use to perform these tasks?
- PLATFORM
- ASSURANCE
- POLICY
- PROVISION
-
A user is reading a book from the website https://www.books-info.com/author50/book1.html#page150 . Which term is used to describe the component www.books-info.com/author50/book1.html ?
- protocol
- fragment
- URN
- URL
- URI
-
Which is a characteristic of EtherChannel?
- EtherChannel configuration is applied to each physical port.
- EtherChannel uses physical ports that have been upgraded to provide a faster connection.
- STP will not block redundant EtherChannel bundles between two switches.
- STP treats all interfaces in an EtherChannel bundle as a single logical link.
-
If no bridge priority is configured in PVST, which criteria is considered when electing the root bridge?
- highest IP address
- highest MAC address
- lowest IP address
- lowest MAC address
Answers Explanation & Hints: Only one switch can be the root bridge for a VLAN. The root bridge is the switch with the lowest BID. The BID is determined by priority and the MAC address. If no priority is configured then all switches use the default priority and the election of the root bridge will be based on the lowest MAC address.
-
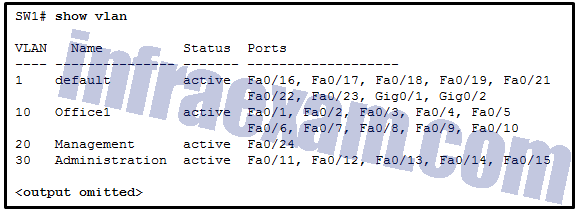
Refer to the exhibit. A network technician issues the command show vlan to verify the VLAN configuration. Based on the output, which port should be assigned with native VLAN?
- Gig0/1
- Fa0/20
- Fa0/24
- Fa0/12
-
An administrator issues the show vlan brief command on a Cisco switch and the output shows that all ports are currently assigned to the default VLAN. What conclusion can be drawn?
- All user data traffic will be separated and secured from other users.
- There is a security risk because the management VLAN and the native VLAN are the same.
- The switch cannot be remotely managed using Telnet or SSH until a management VLAN has been created.
- Layer 2 control traffic is not associated with any VLAN.
-
A network administrator is configuring the SNMP function on a Cisco 3500 series WLC. The task is to add an SNMP trap server to which this WLC will forward SNMP log messages. Which tab should the administrator use to add the SNMP trap server information?
- MANAGEMENT
- MONITOR
- CONTROLLER
- COMMANDS
-
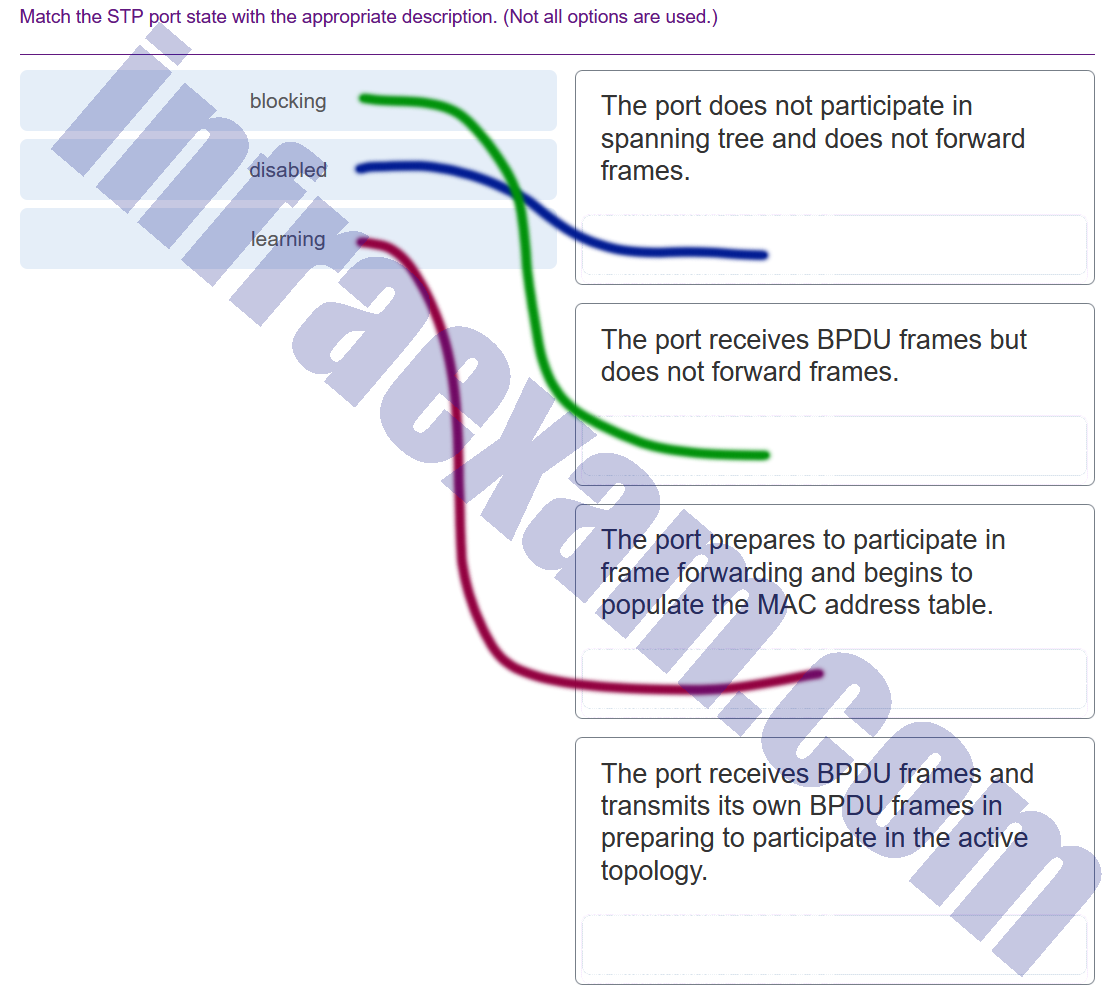
Match the STP port state with the appropriate description. (Not all options are used.)
Answers Explanation & Hints: The details of each port state are shown in the table.
Port State Description Blocking The port is an alternate port and does not participate in frame forwarding. The port receives BPDU frames to determine the location and root ID of the root bridge. BPDU frames also determine which port roles each switch port should assume in the final active STP topology. With a Max Age timer of 20 seconds, a switch port that has not received an expected BPDU from a neighbor switch will go into the blocking state. Listening After the blocking state, a port will move to the listening state. The port receives BPDUs to determine the path to the root. The switch port also transmits its own BPDU frames and informs adjacent switches that the switch port is preparing to participate in the active topology. Learning A switch port transitions to the learning state after the listening state. During the learning state, the switch port receives and processes BPDUs and prepares to participate in frame forwarding. It also begins to populate the MAC address table. However, in the learning state, user frames are not forwarded to the destination. Forwarding In the forwarding state, a switch port is considered part of the active topology. The switch port forwards user traffic and sends and receives BPDU frames. Disabled A switch port in the disabled state does not participate in spanning tree and does not forward frames. The disabled state is set when the switch port is administratively disabled. -
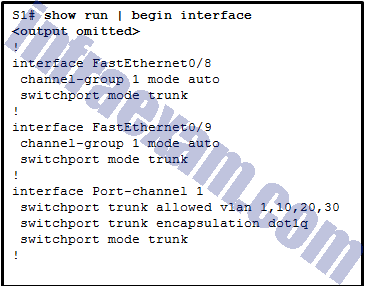
Refer to the exhibit. A network administrator is reviewing the configuration of switch S1. Which protocol has been implemented to group multiple physical ports into one logical link?
- DTP
- LACP
- PAgP
- STP
-
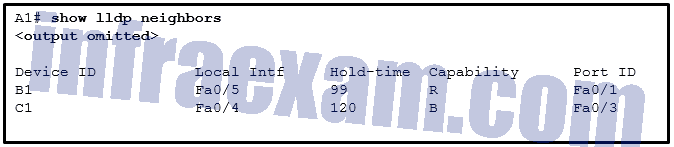
Refer to the exhibit. A network administrator issues the show lldp neighbors command to display information about neighboring devices. What can be determined based on the information?
- Device C1 is a switch.
- Device A1 is connected to the port Fa0/5 on device B1.
- Device C1 is connected to device B1 through the port Fa0/3.
- Device B1 is a WLAN access point.
-
In a controller-based wireless network, the WLC device may have multiple ports connected to a switch to form a bundle that provides load-balancing and redundancy. Which protocol supports the port bundle between a Cisco WLC and a Cisco switch?
- LACP
- CAPWAP
- PAgP
- LAG
-
What are two load-balancing methods in the EtherChannel technology? (Choose two.)
- combination of source MAC and IP to destination MAC and IP
- source port to destination port
- source MAC to destination MAC
- source IP to destination IP
- combination of source port and IP to destination port and IP
Answers Explanation & Hints: Depending on the hardware platform, one or more load-balancing methods can be implemented. These methods include source MAC to destination MAC load balancing or source IP to destination IP load balancing, across the physical links.
-
What is the purpose of setting the native VLAN separate from data VLANs?
- A separate VLAN should be used to carry uncommon untagged frames to avoid bandwidth contention on data VLANs.
- The native VLAN is for carrying VLAN management traffic only.
- The native VLAN is for routers and switches to exchange their management information, so it should be different from data VLANs.
- The security of management frames that are carried in the native VLAN can be enhanced.
-
Refer to the exhibit. A network administrator is reviewing port and VLAN assignments on switch S2 and notices that interfaces Gi0/1 and Gi0/2 are not included in the output. Why would the interfaces be missing from the output?
- They are administratively shut down.
- There is a native VLAN mismatch between the switches.
- There is no media connected to the interfaces.
- They are configured as trunk interfaces.
Answers Explanation & Hints: Interfaces that are configured as trunks do not belong to a VLAN and therefore will not show in the output of the show vlan brief commands.
-
A network engineer is examining the routing table of a Cisco router. Consider the following routing table entry:
S 10.2.2.0/30 [1/0] via 10.1.1.2, 00:00:13, Serial0/0/0
What is the significance of the Serial0/0/0?
- It is the interface on the next-hop router that is directly connected to the 10.2.2.0/30 network.
- It is the R4 interface through which the OSPF update was learned.
- It is the interface on the next-hop router that is directly connected to the 10.1.1.0/24 network.
- It is the interface R4 uses to send data that is destined for 10.2.2.0/30.
-
When two or more routes to the same destination are learned from different routing protocols, what does a router use to choose between the routes?
- administrative distance
- hop count
- metric
- cost
-
A network engineer examining the configuration of a Cisco router sees a network entry in a routing table listed with a code O. Which kind of route is this?
- a static route
- a route used for the default gateway
- a route dynamically learned through the OSPF routing protocol
- a route for a network directly connected to the local router interface
-
Consider the following static route configured on a Cisco router:ipv6 route 2001:db8:acad:4::/64 2001:db8:acad:3::2
What remote network is specified in this route?
- 2001:db8:acad:3::/64
- 2001:db8:acad:0::/64
- 2001:db8:acad:2::0/64
- 2001:db8:acad:4::/64
-
Which two protocols provide gateway redundancy at Layer 3? (Choose two.)
- RSTP
- STP
- HSRP
- VRRP
- PVST
-
A network engineer has been asked to prepare a router and to ensure that it can route IPv6 packets. Which command should the network engineer ensure has been entered on the router?
- ipv6 address
- ipv6 route
- ipv6 enable
- ipv6 unicast-routing
-
What is the purpose of a First Hop Redundancy Protocol?
- to provide a list of IP addresses of devices that can assume the role of the forwarding router
- to provide a dynamic method by which devices on a LAN can determine the address of a new default gateway
- to provide a physical link to a new default router to replace the unreachable default gateway
- to provide two or more routers working together, sharing an IP and MAC address of a virtual default gateway
-
The routing table of a Cisco router has four static routes for network 10.0.0.0. Which route is the best match for a packet entering the router with a destination of 10.16.0.10?
- S 10.16.0.0/16 is directly connected, GigabitEthernet 0/0
- S 10.16.0.0/24 [1/0] via 202.16.0.2
- S 10.0.0.0/16 is directly connected, GigabitEthernet 0/1
- S 10.0.0.0/8 [1/0] via 202.16.0.2
-
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
Which task has to be performed on Router 1 for it to establish an OSPF adjacency with Router 2?
- Remove the passive-interface command from interface FastEthernet 0/0.
- Change the subnet mask of interface FastEthernet 0/0 to 255.255.255.0.
- Issue the clear ip ospf process command.
- Add the network 10.0.1.0 0.0.0.255 area 0 command to the OSPF process.
-
Answers Explanation & Hints: Each interface on the link connecting the OSPF routers must be in the same subnet for an adjacency to be established. The IP address subnet mask on FastEthernet interface 0/0 must be changed to 255.255.255.0. The FastEthernet interface 0/0 is not passive. The 10.0.1.0/24 network is only connected to Router2 so should not be advertised by Router1. The clear ip ospf process command will start the OPSF process on Router1 but will not cause an adjacency to be established if the subnet mask mismatch on the connecting interfaces still exists.
-
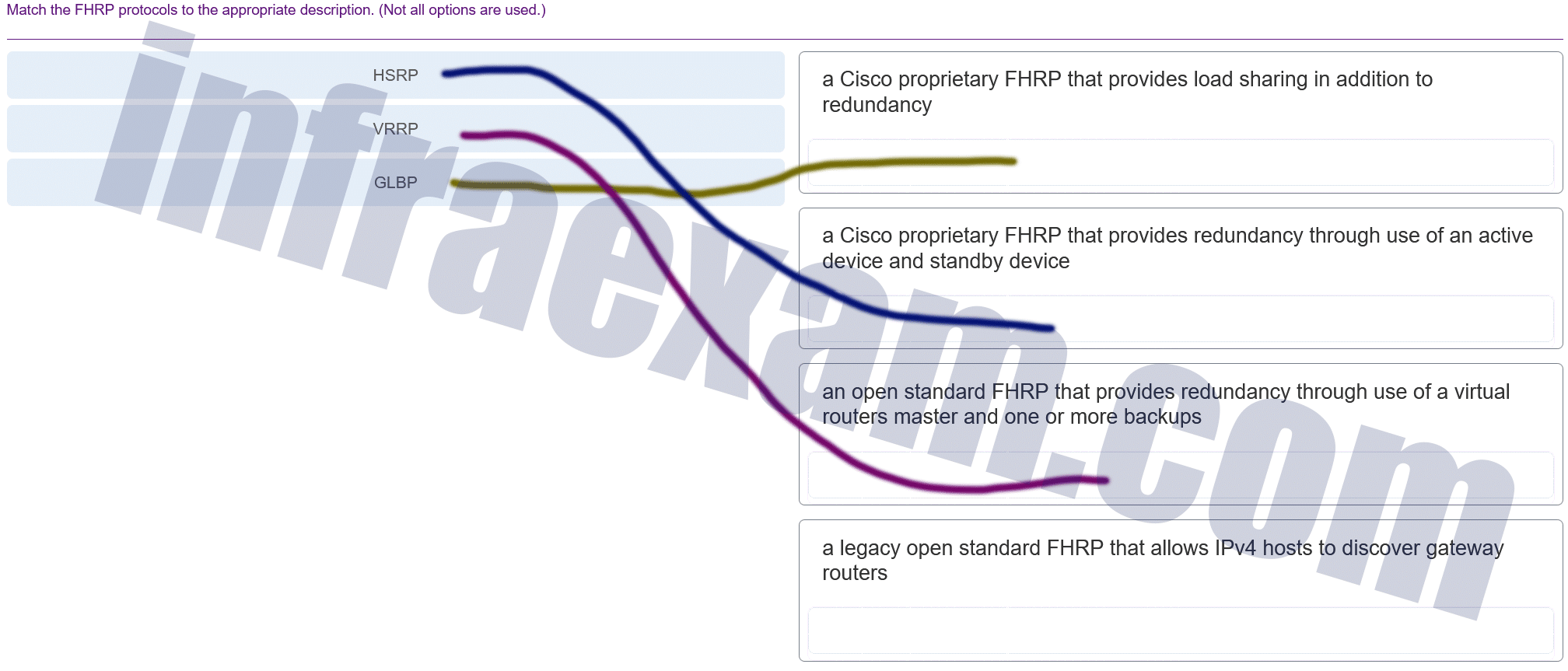
Match the FHRP protocols to the appropriate description. (Not all options are used.)
Answers Explanation & Hints: GLBP, A Cisco proprietary FHRP that provides load sharing in addition to redundancy. HSRP A Cisco proprietary FHRP that provides redundancy through use of an active device and standby device. VRRP, An open standard FHRP that provides redundancy through use of a virtual routers master and one or more backups. Distractor, A legacy open standard FHRP that allows IPv4 hosts to discover gateway routers.
-
What is the recommended Cisco best practice for configuring an OSPF-enabled router so that each router can be easily identified when troubleshooting routing issues?
- Use the highest IP address assigned to an active interface participating in the routing process.
- Use the highest active interface IP address that is configured on the router.
- Use a loopback interface configured with the highest IP address on the router.
Answers Explanation & Hints: A Cisco router is assigned a router ID to uniquely identify it. It can be automatically assigned and take the value of the highest configured IP address on any interface, the value of a specifically-configured loopback address, or the value assigned (which is in the exact form of an IP address) using the router-id command. Cisco recommends using the router-id command.
-
What characterizes a floating static route?
- It serves as a backup to an OSPF-learned route as long as it is configured with an administrative distance of 105.
- It provides load balancing with another static route to the same destination.
- It is a less trustworthy route than the primary route.
- It is configured with a lower administrative distance than the primary router.
-
When creating an IPv6 static route, when must a next-hop IPv6 address and an exit interface both be specified?
- when the next hop is a link-local address
- when the static route is a default route
- when the exit interface is a point-to-point interface
- when CEF is enabled
-
A network administrator configures a router with the ipv6 route ::/0 Serial2/0 command. What is the purpose of this command?
- to enable a router to forward packets for which there is no route in the routing table
- to add a dynamic route for the destination network ::/0 to the routing table
- to forward all packets to the serial 2/0 interface
- to forward packets destined for the network ::/0 to the serial 2/0 interface
-
Which two protocols are used to provide server-based AAA authentication? (Choose two.)
- SNMP
- SSH
- 802.1x
- RADIUS
- TACACS+
-
A wireless network engineer is implementing updated wireless equipment within the company. Which statement describes a wireless security protocol?
- WPA2-Enterprise is intended for enterprise networks and users must authenticate using 802.1X standard.
- WPA secures the data using the Rivest Cipher 4 encryption method with a static key.
- WPA3-Personal uses 802.1X/EAP authentication that requires the use of a 192-bit cryptographic suite.
- WPA2-Personal is intended for home or small office networks and uses 802.1X/EAP authentication.
-
Which security solution identifies incoming threats and blocks them from entering the corporate network?
- firewall filtering
- intrusion prevention systems
- virtual private networks
- access control lists
-
Refer to the exhibit. Which access list configuration on router R1 will prevent traffic from the 192.168.2.0 LAN from reaching the Restricted LAN while permitting traffic from any other LAN?
- R1(config-std-nacl)# deny 192.168.3.0
R1(config-std-nacl)# permit any
R1(config)# interface G0/2
R1(config-if)# ip access-group BLOCK_LAN2 in - R1(config-std-nacl)# deny 192.168.2.0
R1(config-std-nacl)# permit any
R1(config)# interface G0/2
R1(config-if)# ip access-group BLOCK_LAN2 out - R1(config-std-nacl)# permit any
R1(config-std-nacl)# deny 192.168.3.0
R1(config)# interface G0/2
R1(config-if)# ip access-group BLOCK-LAN2 in - R1(config-std-nacl)# permit any
R1(config-std-nacl)# deny 192.168.2.0
R1(config)# interface G0/2
R1(config-if)# ip access-group BLOCK_LAN2 out
- R1(config-std-nacl)# deny 192.168.3.0
-
An employee who travels constantly for work needs to access the company network remotely. Which security mechanism offers a secure connection?
- dedicated firewall system
- access control list
- intrusion prevention system
- virtual private network
-
What is a spyware threat?
- Private information is captured from the network of an organization.
- Software installed on a user device secretly collects information about the user.
- Login credentials of a user are stolen and used to access private data.
- A malicious person attacks user devices or network resources.
-
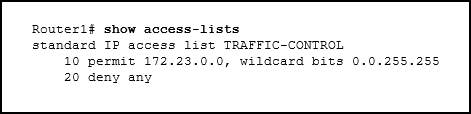
Refer to the exhibit. A network administrator needs to add an ACE to the TRAFFIC-CONTROL ACL that will deny IP traffic from the subnet 172.23.16.0/20. Which ACE will meet this requirement?
- 30 deny 172.23.16.0 0.0.15.255
- 5 deny 172.23.16.0 0.0.15.255
- 5 deny 172.23.16.0 0.0.255.255
- 15 deny 172.23.16.0 0.0.15.255
Answers Explanation & Hints: The only filtering criteria specified for a standard access list is the source IPv4 address. The wild card mask is written to identify what parts of the address to match, with a 0 bit, and what parts of the address should be ignored, which a 1 bit. The router will parse the ACE entries from lowest sequence number to highest. If an ACE must be added to an existing access list, the sequence number should be specified so that the ACE is in the correct place during the ACL evaluation process.
-
Which protocol defines port-based authentication to restrict unauthorized hosts from connecting to the LAN through publicly accessible switch ports?
- TACACS+
- SSH
- 802.1x
- RADIUS
-
What action takes place when the source MAC address of a frame entering a switch appears in the MAC address table associated with a different port?
- The switch resets the refresh timer on all MAC address table entries.
- The switch will forward the frame out all ports except the incoming port.
- The switch replaces the old entry and uses the more current port.
- The switch updates the refresh timer for the entry.
-
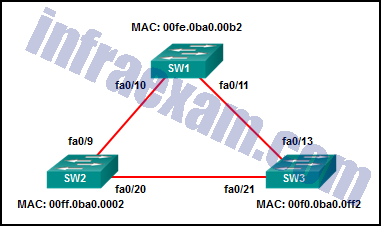
Refer to the exhibit. All the displayed switches are Cisco 2960 switches with the same default priority and operating at the same bandwidth. Which three ports will be STP designated ports? (Choose three.)
- fa0/11
- fa0/21
- fa0/9
- fa0/10
- fa0/13
- fa0/20
-
In a controller-based wireless network, a Cisco WLC device has four ports connected to a switch to form a bundle. This bundle will provide load-balancing and redundancy. Which two configurations must be performed on the four switch ports that connect to the WLC? (Choose two.)
- native VLAN
- default VLAN
- LACP
- EtherChannel
- trunking mode
-
What is the most likely cause when the output of the show interface command shows that a switch interface is up but the line protocol is down?
- An incorrect cable type has been attached to the interface.
- An incorrect default gateway has been configured.
- An encapsulation type mismatch exists.
- A cable is not attached to the interface.
-
A network administrator is configuring a WLAN with WPA2 Enterprise on a Cisco 3500 series WLC. Client authentications will be handled by a RADIUS server. Which tab should the administrator use to add the RADIUS server information?
- WIRELESS
- WLANs
- MANAGEMENT
- SECURITY
-
What is a benefit of PortFast configured on a Cisco switch port?
- It allows a device connected to this port to access the network without waiting for STP convergence on each VLAN.
- It allows the port to avoid a 30 second delay to access the network by immediately transitioning from disabled to forwarding state.
- It avoids the creation of a spanning tree loop with other directly connected switches.
- It minimizes the time that trunk ports must wait for spanning tree to converge.
-
Data is being sent from a source PC to a destination server. Which three statements correctly describe the function of TCP or UDP in this situation? (Choose three.)
- TCP is the preferred protocol when a function requires lower network overhead.
- The TCP source port number identifies the sending host on the network.
- UDP segments are encapsulated within IP packets for transport across the network.
- The TCP process running on the PC randomly selects the destination port when establishing a session with the server.
- The source port field identifies the running application or service that will handle data returning to the PC.
- The UDP destination port number identifies the application or service on the server which will handle the data.
-
What two types of always-on internet connections are commonly used by teleworkers to communicate with a company? (Choose two.)
- cellular
- Metro Ethernet
- DSL
- leased line
- cable
-
A network administrator is considering whether PoE features are required in a specific network installation. Which option provides valid information about PoE?
- Any switch port can be configured with IOS commands to function as a PoE port.
- PoE allows the switch to deliver power to a device over the existing power grid.
- It can be used by IP phones, allowing them to be installed anywhere that there is an Ethernet cable.
- The PoE pass-through feature is only supported by the Cisco Catalyst 3560-C Series compact switch model or higher.
-
A network administrator is designing an IPv4 addressing scheme and requires these subnets.
1 subnet of 100 hosts
2 subnets of 80 hosts
2 subnets of 30 hosts
4 subnets of 20 hostsWhich combination of subnets and masks will provide the best addressing plan for these requirements?
- 1 subnet of 126 hosts with a 255.255.255.192 mask
2 subnets of 80 hosts with a 255.255.255.224 mask
6 subnets of 30 hosts with a 255.255.255.240 mask - 3 subnets of 126 hosts with a 255.255.255.128 mask
6 subnets of 30 hosts with a 255.255.255.224 mask - 3 subnets of 126 hosts with a 255.255.255.192 mask
6 subnets of 30 hosts with a 255.255.255.240 mask - 9 subnets of 126 hosts with a 255.255.255.128 mask
- 1 subnet of 126 hosts with a 255.255.255.192 mask
-
An instructor is reviewing student answers on a previous term exam to prepare for a lecture on IPv6. What would be a good point for the instructor to make when explaining an IPv6 GUA (global unicast address)?
- It can be configured statically or assigned dynamically on a router.
- It is routable on the IPv6 internet.
- It is considered a best practice to use the IPV6 GUA address of the router as the default gateway address for Windows hosts.
- It can only be configured statically on a host interface by using the ipv6 address command.
-
How are network data transmissions calculated?
- goodput + latency = bandwidth
- throughput + goodput = bandwidth
- goodput + traffic overhead = throughput
- throughput + latency = goodput
-
What action takes place when a frame entering a switch has a multicast destination MAC address?
- The switch adds a MAC address table entry mapping for the destination MAC address and the ingress port.
- The switch will forward the frame out all ports except the incoming port.
- The switch forwards the frame out of the specified port.
- The switch replaces the old entry and uses the more current port.
-
In FHRP terminology, what represents a set of routers that present the illusion of a single router to hosts?
- virtual router
- standby router
- default gateway
- forwarding router
Answers Explanation & Hints: In FHRP multiple routers are configured to work together to present to hosts a single gateway router. This single gateway router is a virtual router which has a virtual IP address that is used by hosts as a default gateway.
-
Which feature on a Cisco router permits the forwarding of traffic for which there is no specific route?
- outgoing interface
- next-hop
- gateway of last resort
- route source
-
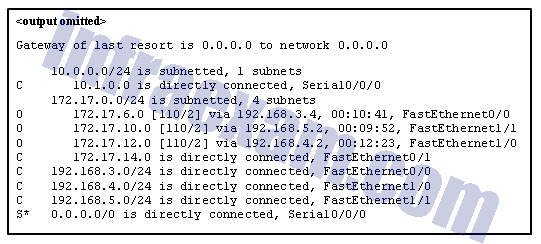
Refer to the exhibit. Match the packets with their destination IP address to the exiting interfaces on the router. (Not all targets are used.)
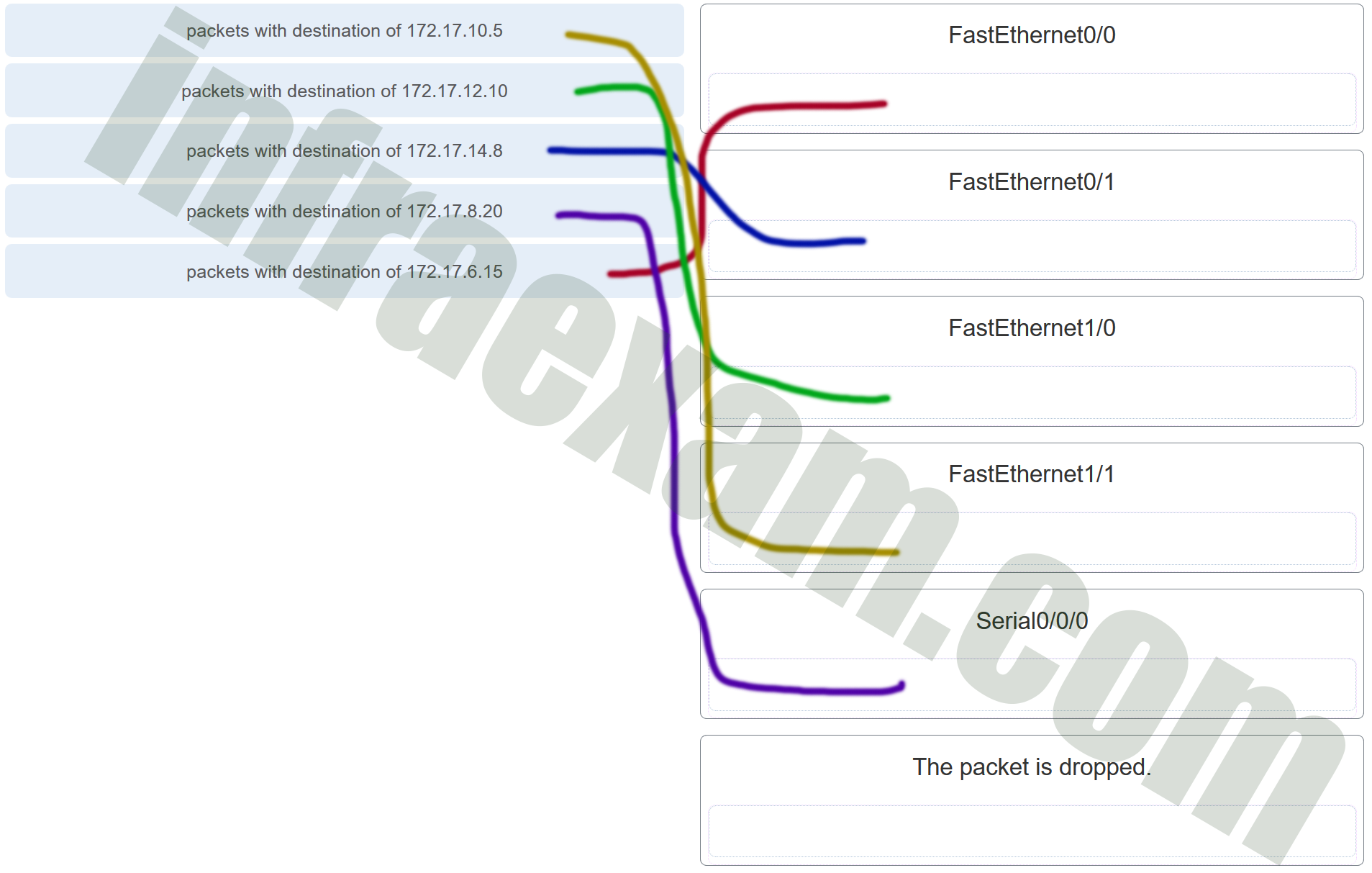
CCNA1 v7 – ITNv7 – Modules 8 – 10 Communicating Between Networks Exam Answers 001
Answers Explanation & Hints: Packets with a destination of 172.17.6.15 are forwarded through Fa0/0. Packets with a destination of 172.17.10.5 are forwarded through Fa1/1. Packets with a destination of 172.17.12.10 are forwarded through Fa1/0. Packets with a destination of 172.17.14.8 are forwarded through Fa0/1. Because network 172.17.8.0 has no entry in the routing table, it will take the gateway of last resort, which means that packets with a destination of 172.17.8.20 are forwarded through Serial0/0/0. Because a gateway of last resort exists, no packets will be dropped.
-
What defines a host route on a Cisco router?
- A host route is designated with a C in the routing table.
- An IPv4 static host route configuration uses a destination IP address of a specific device and a /32 subnet mask.
- The link-local address is added automatically to the routing table as an IPv6 host route.
- A static IPv6 host route must include the interface type and the interface number of the next hop router.
-
A network engineer is examining Cisco router configurations across an internetwork. Consider the following routing table entry
O 10.0.4.0/24 [110/50] via 10.0.3.2, 00:24:22, Serial0/1/1
What is the administrative distance of this route?
- 110
- 24
- 160
- 50
-
Which term describes the process of managing configuration changes of network devices in an orderly fashion?
- provisioning
- automation
- orchestration
- version control
-
A programmer is using Ansible as the configuration management tool. Which term is used to describe a set of instructions for execution?
- Pillar
- Cookbook
- Manifest
- Playbook
-
In an Intent-Based Networking architecture, which two items are considered parts of an overlay fabric? (Choose two.)
- IPsec protocol
- switch
- server
- router
- CAPWAP
-
Which LAN attack involves the sending of a double-tagged 802.1Q frame to the switch?
- VLAN double-tagging attack
- DHCP spoofing attack
- DHCP starvation attack
- VLAN hopping attack
-
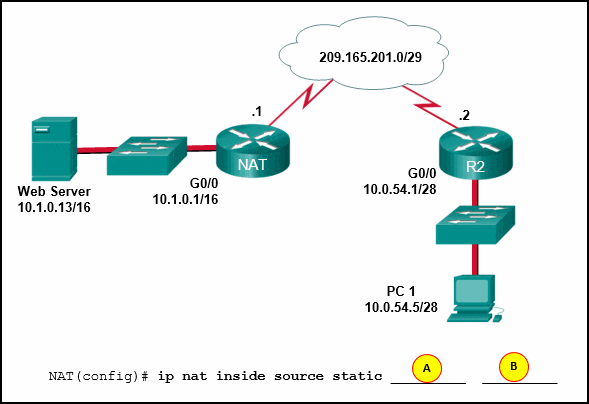
Refer to the exhibit. Static NAT is being configured to allow PC 1 access to the web server on the internal network. What two addresses are needed in place of A and B to complete the static NAT configuration? (Choose two.)
- B = 209.165.201.7
- A = 209.165.201.2
- A = 10.1.0.13
- B = 209.165.201.1
- B = 10.0.254.5
Answers Explanation & Hints: Static NAT is a one-to-one mapping between an inside local address and an inside global address. By using static NAT, external devices can initiate connections to internal devices by using the inside global addresses. The NAT devices will translate the inside global address to the inside local address of the target host.
-
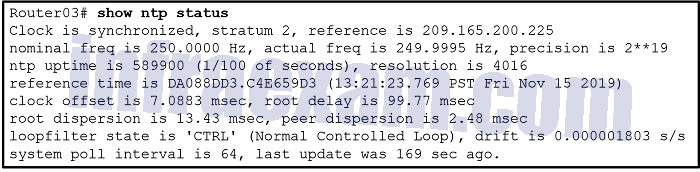
Refer to the exhibit. A corporate network is using NTP to synchronize the time across devices. What can be determined from the displayed output?
- The interface on Router03 that connects to the time sever has the IPv4 address 209.165.200.225.
- Router03 is a stratum 2 device that can provide NTP service to other devices in the network.
- The time on Router03 may not be reliable because it is offset by more than 7 seconds to the time server.
- Router03 time is synchronized to a stratum 2 time server.
-
In computer network communications which data transfer process does the application layer protocol FTP use?
- client-server
- server message block
- peer-to-peer
- Gnutella
-
When configuring a switch for SSH access, what other command that is associated with the login local command is required to be entered on the switch?
- username username secret secret
- enable secret password
- password password
- login block-for seconds attempts number within seconds
-
A network administrator of a college is configuring WLAN security with WPA2 Enterprise authentication. Which server is required when deploying this type of authentication?
- DHCP
- RADIUS
- SNMP
- AAA
Answers Explanation & Hints: WAP2 Enterprise provides stronger secure user authentication than WPA2 PSK does. Instead of using a pre-shared key for all users to access a WLAN, WPA2 Enterprise requires that users enter their own username and password credentials to be authenticated before they can access the WLAN. The RADIUS server is required for deploying WPA2 Enterprise authentication.
-
An administrator who is troubleshooting connectivity issues on a switch notices that a switch port configured for port security is in the err-disabled state. After verifying the cause of the violation, how should the administrator re-enable the port without disrupting network operation?
- Reboot the switch.
- Issue the no switchport port-security violation shutdown command on the interface.
- Issue the shutdown command followed by the no shutdown command on the interface.
- Issue the no switchport port-security command, then re-enable port security.
Answers Explanation & Hints: To re-enable the port, use the shutdown interface configuration mode command (Figure 3). Then, use the no shutdown interface configuration command to make the port operational.
-
When configuring a wireless LAN, to which category does a home wireless router belong?
- autonomous AP
- LWAPP-protocol based
- controller-based AP
- CAPWAP-protocol based
-
A company deploys FlexConnect APs in the remote office and uses CAPWAP to allow a WLC in their corporate headquarters office to manage WLANs in the remote office. One day the network administrator in the remote office notices that the FlexConnect APs are operating in the standalone mode. Which two functions can these APs perform in this mode? (Choose two.)
- re-association of roaming clients
- switching client data traffic locally
- association of roaming clients
- client authentication locally
- frame translation to other protocols
-
What characteristic describes how data or voice VLANs are configured on a network?
- A switch port that has been configured in access mode can only belong to one data VLAN at a time.
- The switchport access vlan command must specify a VLAN currently configured in the vlan.dat file.
- Data and voice VLANs have a different value range for VLAN IDs.
- Voice VLANs are configured on a trunk link between the IP phone and the switch.
-
What action takes place when a frame entering a switch has a broadcast destination MAC address?
- The switch adds a MAC address table entry mapping for the destination MAC address and the ingress port.
- The switch replaces the old entry and uses the more current port.
- The switch will forward the frame out all ports except the incoming port.
- The switch forwards the frame out of the specified port.
-
An employee is logging into a company account and another employee stands in such a way to see the account ID and password. Which kind of threat is this?
- adware
- spyware
- data interception and theft
- identity theft
-
When testing a new web server, a network administrator cannot access the home page when the server name is entered into a web browser on a PC. Pings to both the IPv4 and IPv6 addresses of the server are successful. What could be the problem?
- ARP is not discovering the MAC address of the server.
- DHCP has not assigned an IPv4 or IPv6 address to the server.
- DNS is not resolving the server name to an IPv4 or IPv6 address.
- An FTP client must be installed on the PC.
-
SNMP has been implemented on a network to monitor and manage devices. Which SNMP authentication process is preferred when SNMP managers communicate with SNMP agents?
- MD5 or SHA authentication
- username authentication
- plain-text community string
- community string encryption
-
Which function of the Cisco intent-based networking system (IBNS) enables network operators to express the expected networking behavior that will best support the business intent?
- assurance
- activation
- translation
- ACL analysis
-
What is an architectural constraint to which a true RESTful API web service must adhere?
- It operates as a cloud service.
- It uses HTTPS to transport data.
- It must support the XML data format.
- It runs as client/server model.
-
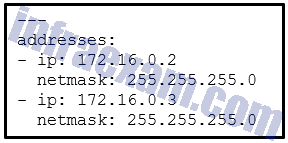
Refer to the exhibit. What does the hyphen symbol (–) indicate in the YAML data structure?
- an element in an array
- a key/value pair that represents an IP address
- a single key/value pair
- a string being used for both the key and value
-
Which two statements describe an Internet-based connectivity option? (Choose two.)
- In cable technology, each local subscriber has a separate direct connection to the provider headend.
- LTE is a newer 5G mobile access technology.
- VPNs provide security for teleworkers who use DSL to access the corporate network through the internet.
- ADSL2+ provides higher upload bandwidth than downstream bandwidth.
- When using a satellite to connect to the internet, the reception of signals can be affected by storms.
-
Two students are discussing routers and one statement that is said between them is accurate. Which statement is that?
- A gateway of last resort is added to the routing table when the router boots up.
- Remote networks can only be added after they are learned by routers through dynamic routing protocols.
- A directly-connected network is automatically added to the routing table of an adjacency neighbor if both routers are Cisco routers.
- A default route provides a way for packets that do not match a specific route in the routing table to be forwarded.
-
Which LAN attack involves sending unsolicited ARP replies, with the MAC Address of the threat actor and the IP address of the default gateway, to other hosts on a subnet?
- ARP attack
- address spoofing attack
- DHCP starvation attack
- DHCP spoofing attack
-
What characteristic completes the following statement?
When an IPv6 static route is configured, a fully-specified configuration should be used with ……
- the next-hop address of two different adjacent routers.
- a directly connected multiaccess network.
- an administrative distance of 2.
- the “ipv6 unicast-routing” command.
-
What term describes a process where a router simply discards any packet that arrives at the end of a queue that has completely used up its packet-holding resources?
- latency
- tail drop
- jitter
- congestion
- bandwidth